Small businesses are increasingly becoming targets for cybercriminals. With limited resources and often less robust security measures, they can be seen as easy prey. However, small businesses can significantly enhance their cybersecurity posture by implementing the following tips and best practices.
Year: 2024
Check out how AI is Transforming Cybersecurity
Artificial Intelligence (AI) is revolutionizing various sectors, and cybersecurity is no exception. By automating threat detection, improving response times, and enhancing overall security measures, AI is becoming an integral part of modern cybersecurity strategies. Here’s a detailed look at how AI is transforming cybersecurity
Knowing the Importance of Cybersecurity in Remote Work
The shift to remote work has brought significant changes to the business landscape, offering flexibility and convenience but also introducing new cybersecurity challenges. As more employees work from home, organizations must adapt their security strategies to protect sensitive information and maintain operational integrity. Here’s why cybersecurity is crucial in the remote work environment and how organizations can enhance their security posture.
Top 10 Cybersecurity Threats in 2024
Cybersecurity threats continue to evolve, posing significant risks to individuals, businesses, and governments. Here are the top 10 cybersecurity threats to watch out for in 2024
Step by step Introduction to CSS for web Development
You will learn how to use CSS to control the style and layout of multiple Web pages all at once.
With your editor, you can edit the CSS rule and see your result in your browser.
Step by step on how to program with HTML Language
HTML (HyperText Markup Language) is the standard markup language used to create and design documents on the World Wide Web. Here are the key aspects of HTML: Structure: HTML provides the basic structure of web pages, which is enhanced and modified by other technologies like CSS (Cascading Style Sheets) and JavaScript. Elements: HTML consists of a series of elements, which you use to enclose, or wrap, different parts of the content to make it appear a certain way or act a certain way. Examples include headings, paragraphs, links,…
100% Working way to Recover Deleted File
Losing files is very upseting. Every now and then, we go through unfortunate situations. One such situation is accidental deletion of your important file. It could be a document, image or a video. Regardless of what type of file you have just lost, nothing is harder for the best free data recovery software – EaseUS.
Software for building a website and step by step process to build a website
Building a website involves several steps, from initial planning to the final launch. Here’s a comprehensive guide: Define the purpose of your website. Is it for a business, blog, portfolio, e-commerce, etc.
Step by step on using Acunetix for web vulnerability scanning
Acunetix is a popular web vulnerability scanner designed to identify security issues in web applications. Here’s a step-by-step guide on how to use Acunetix for web vulnerability scanning
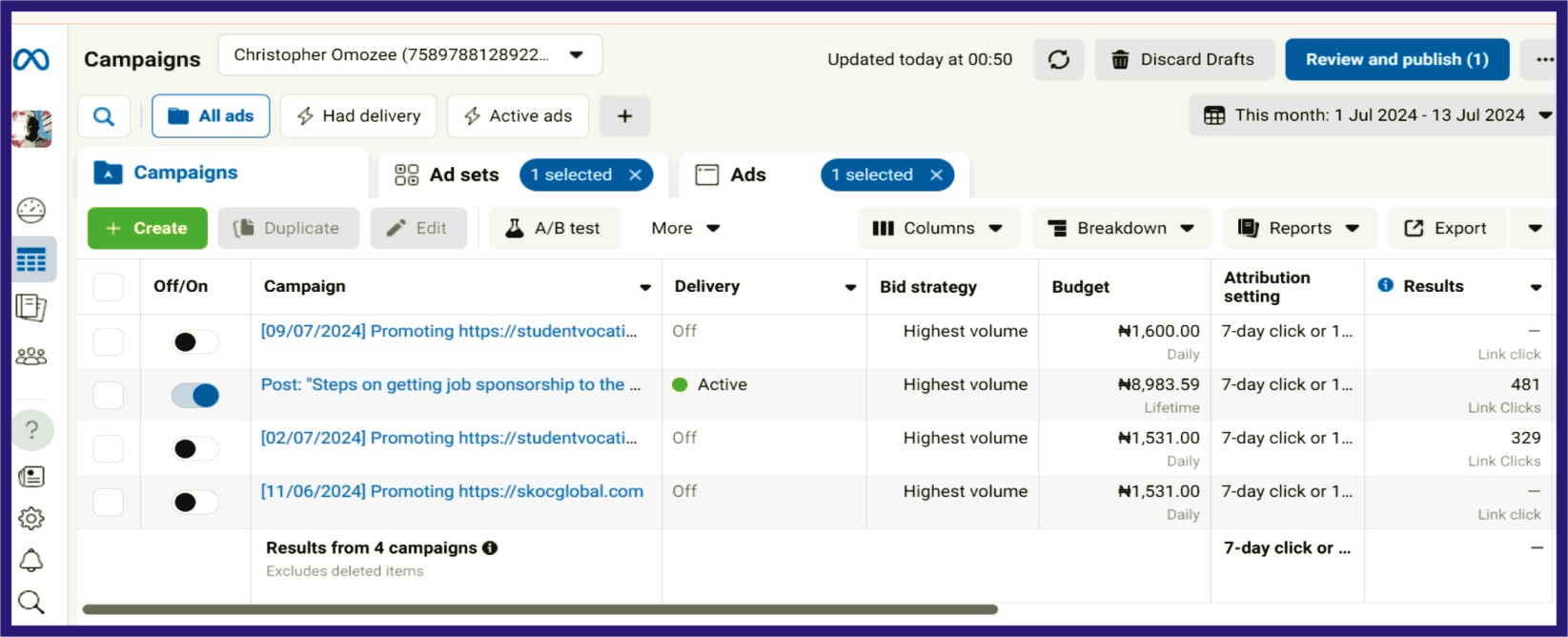
How can i promote a website using facebook
Promoting a website on Facebook can be highly effective, given the platform’s vast user base and diverse advertising tools. Here are some strategies to help you promote your website effectively