Storage is an essential part of every computer system, as it determines how data is stored, accessed, and retrieved. There are several types of storage devices, each with different speeds, capacities, and use cases.
Author: adminstud
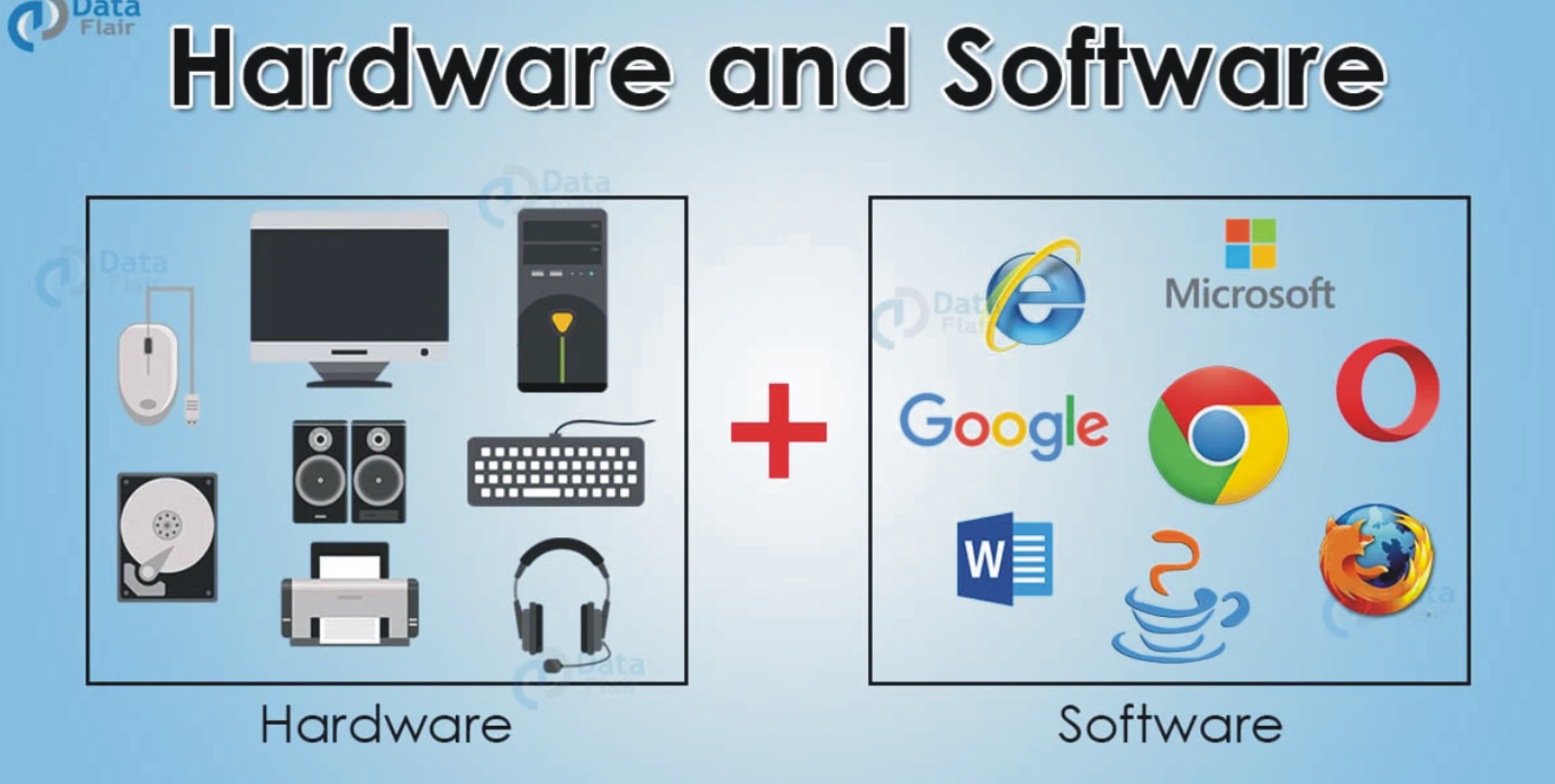
Understanding Hardware vs. Software: Key Differences Explained
Computers and digital devices operate using two essential components: hardware and software. While hardware refers to the physical parts of a device, software consists of the programs and instructions that make the hardware functional.
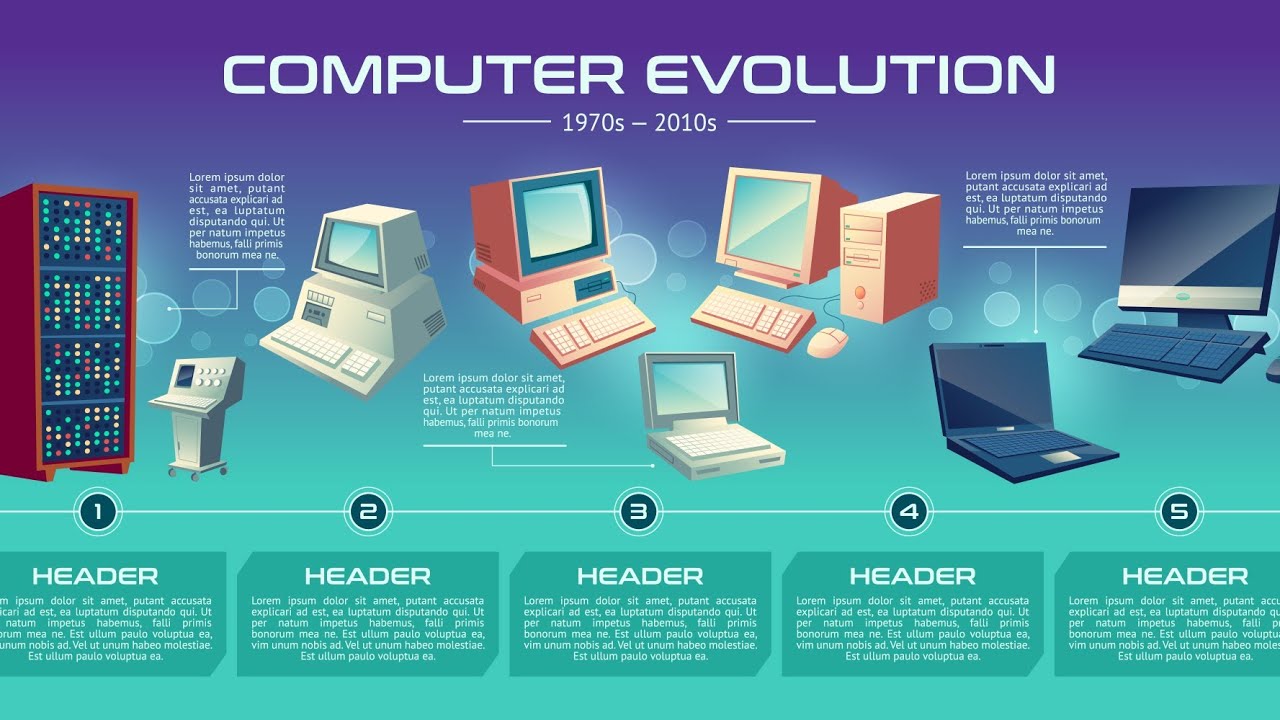
The Evolution of Computers: From ENIAC to AI-Powered Systems
Computers have come a long way from the massive, room-sized machines of the 1940s to the sleek, AI-powered systems we use today. Their evolution has been driven by advancements in technology, making them smaller, faster, and more intelligent.
What is ICT? A Beginner’s Guide to Information and Communication Technology
Information and Communication Technology (ICT) is a broad term that refers to the integration of computing, networking, and telecommunications technologies.
The Ultimate Checklist for Launching Your First Website
The Ultimate Checklist for Launching Your First Website. Here’s your Ultimate Checklist for Launching Your First Website
How to Teach Kids About ICT in a Fun Way
Here’s a structured guide on How to Teach Kids About ICT in a Fun Way
ICT for Small Businesses: Why It Matters
Information and Communication Technology (ICT) is a game-changer for small businesses, helping them compete with larger companies, improve efficiency, and reach more customers
The Role of ICT in Modern Healthcare
Information and Communication Technology (ICT) has revolutionized the healthcare industry, improving patient care, medical research, and hospital management.
How to Stay Updated with ICT Trends
Technology evolves rapidly, and staying informed about ICT trends is essential for professionals, students, and businesses. Whether you’re in web design, cybersecurity, AI, or networking, keeping up with the latest developments helps you stay competitive.
Top 5 ICT Movies and What They Teach Us
Movies can be an entertaining way to learn about ICT, hacking, cybersecurity, artificial intelligence, and the impact of technology on society. Here are five must-watch ICT-related films and the lessons they teach us.