From advancements in artificial intelligence to innovations in quantum computing and sustainability, 2024 is shaping up to be a dynamic year for technology.
Month: October 2024
Key Differences between Quantum Computing vs. Classical Computing
Quantum and classical computing operate on fundamentally different principles, leading to distinct strengths and applications. Below is a detailed comparison of these two paradigms.
Quantum Computing Applications Across Industries
Quantum computing is poised to revolutionize industries by solving complex problems that are beyond the capabilities of classical computers. Below are some of the key applications of quantum computing across various fields.
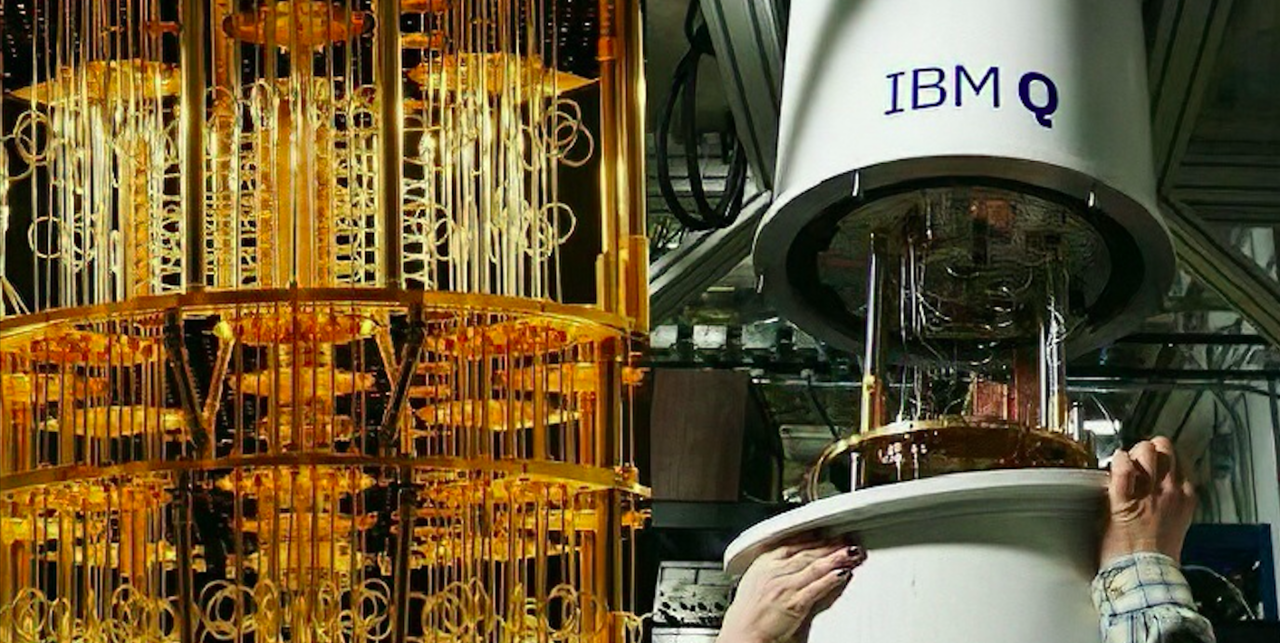
What you should know about quantum computing
Quantum computing is a cutting-edge field of computer science that leverages the principles of quantum mechanics—the fundamental theory governing the behavior of subatomic particles—to process information.
Why the Demand for Cybersecurity Skills Keeps Growing
The increasing importance of cybersecurity is driven by the rapid evolution of digital technology and the ever-expanding threat landscape.
Ethical Hacking vs. Black Hat Hacking: Key Differences
While both ethical hackers and black hat hackers possess similar technical skills, their intentions, methods, and outcomes are vastly different.
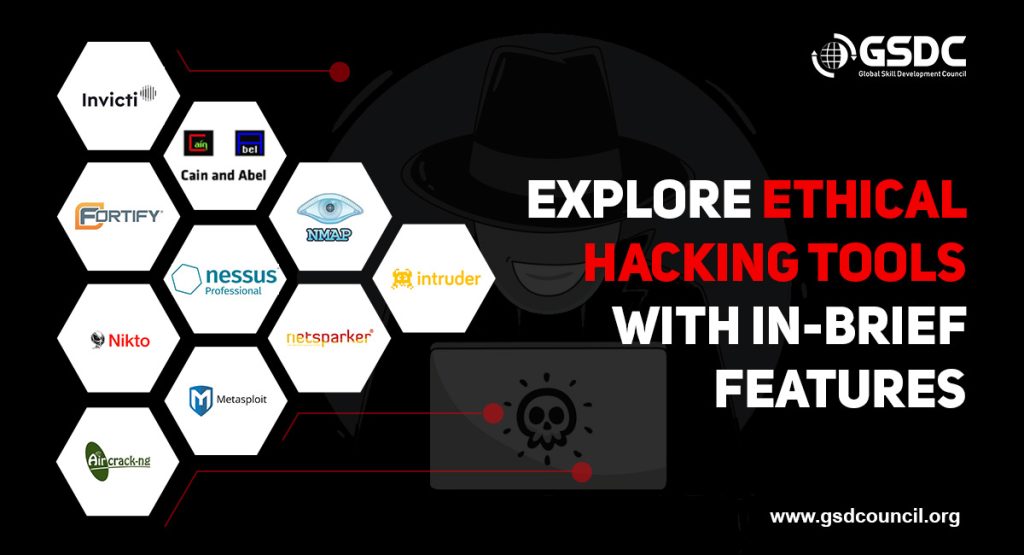
Nine top Ethical Hacking Tools to be aware of
Ethical hackers use specialized tools to detect vulnerabilities, test defenses, and simulate cyberattacks. Below are some of the most popular and effective tools for various hacking tasks, including network scanning, web testing, password cracking, and exploitation.
Get to know What is Penetration Testing
Penetration Testing (or Pen Testing) is a cybersecurity practice where professionals simulate real-world attacks on a computer system, network, or web application to identify vulnerabilities.
Knowing the importance of Ethical Hacking Courses
Ethical Hacking Courses help individuals gain the skills needed to protect systems by thinking like a hacker. These courses cover areas such as penetration testing, vulnerability assessment, and security auditing.
The Importance of Remote Work Security for employees
Remote Work Security is essential as employees increasingly work outside traditional office environments, exposing businesses to unique cyber risks.