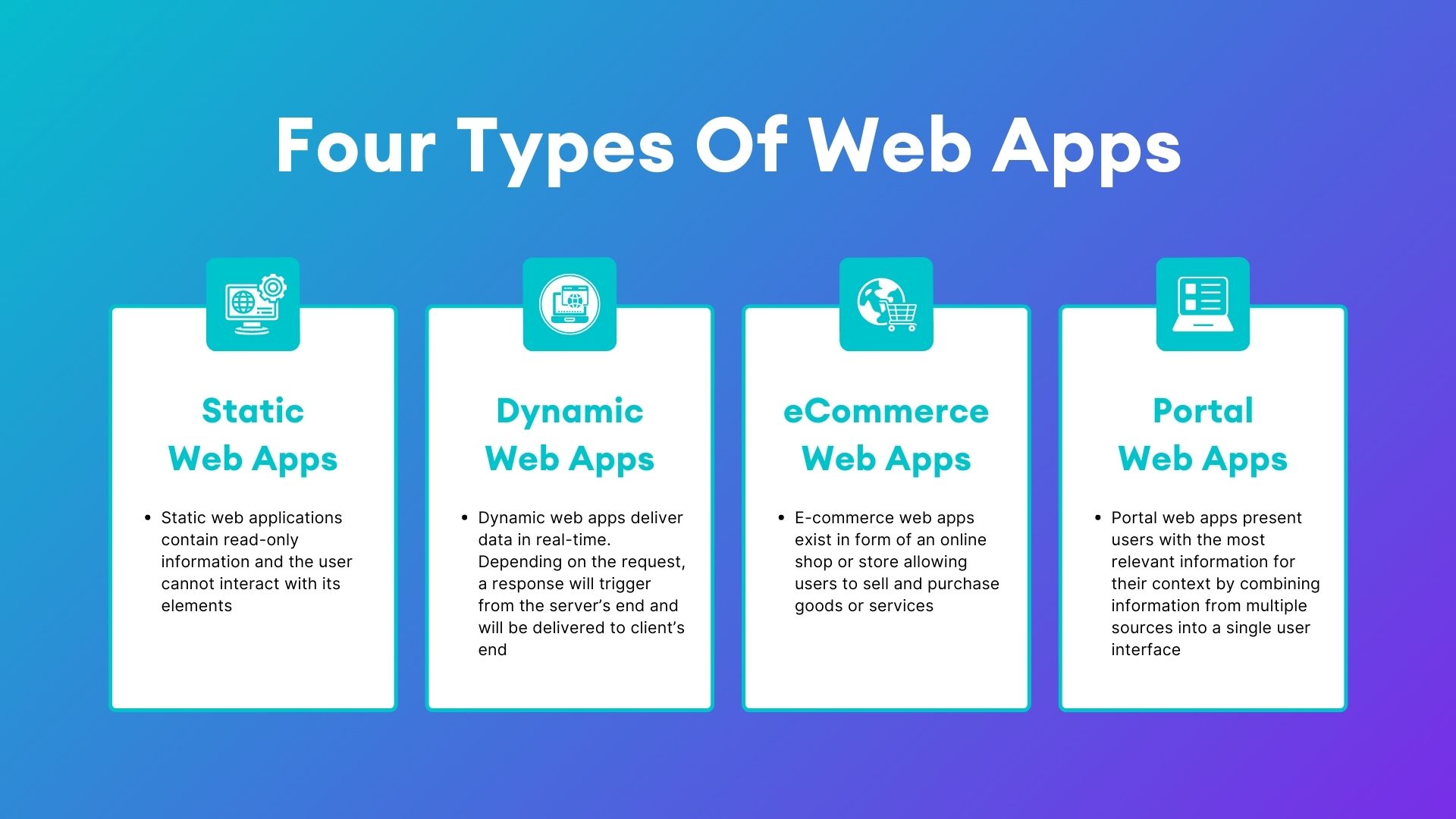
A web application (or web app) is a software program that operates through a web browser and is accessed over the internet.
Category: Development
The Power of Website Analytics: How to Track and Improve Your Site
Website analytics is a powerful tool that enables you to understand how visitors interact with your site, identify areas for improvement, and make data-driven decisions to enhance performance.
How to Create a Blog and Start Writing Online
Starting a blog is an excellent way to share your ideas, build a personal brand, or even create a source of income.
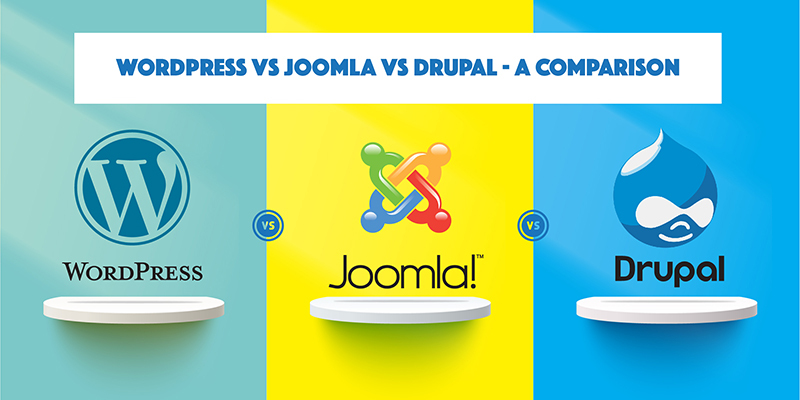
What is CMS? Comparing WordPress- Joomla and Drupal
A CMS is software that allows users to create and modify content typically websites without needing to write code from scratch.
How to Create a Simple Contact Form Using HTML CSS and JavaScript
Creating a simple contact form using HTML, CSS, and JavaScript involves structuring the form with HTML, styling it with CSS, and adding interactivity and validation with JavaScript.
Introduction to PHP: The Language Behind Dynamic Websites
PHP (Hypertext Preprocessor) is a widely-used open-source server-side scripting language designed for web development. It enables developers to create dynamic and interactive websites by embedding PHP code within HTML
Basics of SEO: How to Make Your Website Rank on Google
Optimizing your website for search engines is essential to increase visibility, attract more visitors, and grow your online presence. Here’s a beginner-friendly guide to help you understand and implement effective SEO strategies
How to Optimize Website Speed and Performance
Optimizing your website’s speed and performance is crucial for enhancing user experience, improving search engine rankings, and increasing conversion rates. Here are some effective strategies to achieve this
Introduction to Web Accessibility: Designing for Everyone
Web accessibility ensures that websites, tools, and technologies are designed and developed so that people with disabilities can use them effectively.
Essential Web Design Tools Every Designer Should Know
Below are the most essential web-design tools organized by category. Each tool has become a de facto standard in its area—whether you’re mocking up interfaces, writing code, collaborating with developers, testing responsiveness, or sourcing assets—so mastering these will significantly boost your productivity and the quality of your work.